By Rich Heidorn Jr.
FERC announced Thursday it was rethinking its cybersecurity strategy by reorganizing two departments and directing its efforts at five “focus areas.”
The changes resulted from Chairman Neil Chatterjee’s directive that the Office of Electric Reliability (OER), the Office of Energy Infrastructure Security (OEIS) and the Office of Energy Projects (OEP) identify ways they can combine their cybersecurity efforts.
As a result of that review, OEP is creating a unit within the Division of Dam Safety and Inspections staffed by physical and cybersecurity specialists.
In addition, OER will reorganize based on functions effective Sunday, with the Division of Reliability Standards and Security and the Division of Compliance realigned into the Division of Operations and Planning Standards and the Division of Cybersecurity.
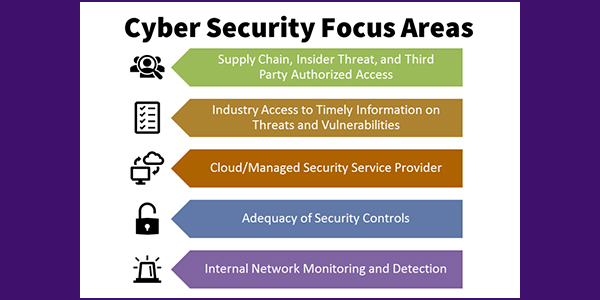
FERC also identified five subject areas that will guide FERC staff efforts:
- Supply Chain/Insider Threat/Third-Party Authorized Access: Ways an attacker can bypass perimeter security controls.
- Industry access to timely information on threats and vulnerabilities: A recognition that many entities have limited threat intelligence capabilities and access to information on threats.
- Cloud/Managed Security Service Providers: A recognition that delegating trusted third parties to perform common services can have security benefits while also calling for more research to determine if the most critical systems, such as those used for real-time operations, could be moved to the cloud.
- Adequacy of security controls: Although low-impact bulk electric system cyber systems (BCS) make up the majority of BES cyber assets, they are generally not subject to mandatory security controls. The simultaneous loss or degradation of a large number of these systems could have a significant impact. Many commission jurisdictional hydroelectric facilities and natural gas pipelines are not subject to mandatory cybersecurity controls.
- Internal network monitoring and detection: Internal monitoring of protected networks is not required by NERC critical infrastructure protection (CIP) standards; a failure to conduct monitoring can allow attackers to move laterally within “trust zones.”
Staff identified the focus areas based on a review of public and nonpublic threat reports, significant cybersecurity events impacting industrial infrastructure and CIP standards.
“Staff will continue to monitor entities’ supply chain security implementation and use of trusted connections,” staffers said in a presentation at the commission’s open meeting Thursday. “Additionally, staff will monitor entities’ adoption of new technologies and services to address cyber infrastructure implementation [including] virtualization of systems and use of cloud-computing services. Staff will continue to gather information and work with regulated entities on these issues as well as potential modifications to the CIP standards, such as the security controls for low-impact BES cyber systems.”
Staff noted that OEIS offers voluntary network architecture assessments of electric, hydroelectric, natural gas and LNG facilities, working with other federal agencies such as the Department of Homeland Security, the Transportation Security Administration and the Coast Guard.
Hydro Security, Internal Monitoring
FERC said the additional security capabilities for OEP will build on the Security Program for Hydropower Projects, created in response to the Sept. 11, 2001, terrorist attacks and revised three times since.
“The program’s been enhanced over the years,” David Capka, director of the dam safety division, explained in response to a question from the chairman after the presentation. “However, when cybersecurity became part of the program, within OEP we had to rely heavily on experts outside our office. So, we relied on OEIS and OER to help us. And it quickly became clear that we needed in-house … expertise.”
Capka said the changes will have two benefits. “I think we’re going to have a much more robust security program with the expertise we’ve been able to bring on board. [And] we’re allowing our dam safety engineers to focus on dam safety now.”
OER’s Barry Kuehnle responded to a question from Commissioner Bernard McNamee about the need for internal network monitoring to prevent hackers from being able to make undetected lateral movement within a “trust zone.”
“If someone were to gain access [within a safety perimeter] — suppose they come in with a supply chain attack where you purchase a piece of equipment with a back door in it — you put that into the network, now it’s an authenticated piece of equipment … that potentially may end up … communicating with other equipment within that network,” Kuehnle said. “If you’re … looking for anomalies … you can catch that quicker and you’re able to address any type of security concerns.”