ERCOT is working with federal officials to investigate a cybersecurity incident that resulted in the ISO sending a number of wire transfers to a fraudulent bank account last week.
In a market notice issued Friday, ERCOT said the incident began when an attacker compromised a Microsoft Office 365 account belonging to one of its market participants, who was not named in the report. Using the compromised account, the attacker gained access to the email address of the market participant’s authorized representative. It then created several additional email accounts that appeared nearly identical to those of officers and employees at the market participant (a technique known as “domain typo-squatting”).
ERCOT became involved on April 20, when the attacker used the authorized representative’s email account to request the ISO modify the market participant’s banking information. After ERCOT granted the request, a number of wire transfers intended for the market participant were sent to the new bank account from April 21 to 23, when the market participant notified ERCOT that its registration information may have been compromised.
Working with federal authorities, ERCOT was able to recover “a majority” of the transfers sent to the fraudulent account and is still attempting to recover the remaining funds. The identity of the attacker has not been determined. According to the ISO, several IP addresses in Germany and Ghana were used in the attack.
ERCOT’s Computers Not Compromised
ERCOT defines a cybersecurity incident as “a malicious or suspicious act that compromises or disrupts a computer network or system that could foreseeably jeopardize the reliability or integrity of the ERCOT system or ERCOT’s ability to perform the functions of an independent organization.” While the attack meets this definition because it impacted ERCOT’s ability to perform certain registration functions, at this time the ISO has found no evidence that its computer networks or systems were compromised as a result of the attack.
The only computer or network to be compromised appears to be the single Office 365 account belonging to the affected market participant, who ERCOT said had not enabled multi-factor authentication (MFA). ERCOT recommends all participants use MFA to help prevent unauthorized individuals from accessing sensitive information.
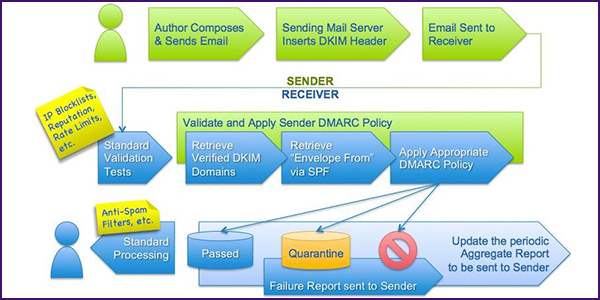
It also suggested other protective methods, such as pre-registering email domains similar to those used by market participants and using a domain-based message authentication reporting and conformance (DMARC) practice to ensure only legitimate emails reach their intended recipients.
ERCOT began using DMARC last year. It said that in 2018 several million fraudulent or deceptive emails were sent using the @ercot.com domain. ERCOT’s practice authenticates outgoing emails from the @ercot.com domain and prevents any that fail the DMARC test from reaching any recipient that has a DMARC practice in place.
The ISO is implementing “additional levels of control” for changes to banking information and plans to discuss in future stakeholder meetings additional controls on updates to market participants’ registration information.
ERCOT said the incident seems to be unconnected to a data breach at JPMorgan Chase Bank in March that inadvertently disclosed account information for some ERCOT counterparties.
Cybersecurity has been identified as a significant concern for the electrical industry, due to the large number of people using online services, including Office 365, Slack, and others, to work from home. In a recent report NERC recommended industry be “hyper vigilant” because “a distracted workforce and remote working arrangements open up new attack vectors.” The organization urged utilities to use the E-ISAC and the Cybersecurity Risk Information Sharing Program to stay abreast of the latest threats. (See PPE, Testing Top Coronavirus Concerns for NERC.)