
Cybersecurity firm Dragos, a partner of the Electricity Information Sharing and Analysis Center (E-ISAC), this week suffered a cyber breach that exposed customer information, E-ISAC CEO Manny Cancel revealed at a meeting of NERC’s Technology and Security Committee on Wednesday.
Cancel assured listeners that none of the E-ISAC’s data was compromised in the breach. However, he said that “out of an abundance of caution” the E-ISAC had disabled Dragos’ access to its network for the time being.
The organization has partnered with Dragos to share information about threat analytics and indicators of compromise through the firm’s Neighborhood Keeper threat intelligence system. (See E-ISAC Joins Dragos for Data Sharing Initiative.) In addition, Dragos helps analyze data submitted through the E-ISAC’s Cybersecurity Risk Information Sharing Program.
Access Gained Through New Employee Account
The intrusion occurred on May 8, Dragos said in a blog post Wednesday. The firm did not name the group responsible for the attack but said the perpetrator was a “known cybercriminal group” that typically tries to install ransomware on target systems. Cancel said the attackers are “suspected to be a foreign … ransomware service that is probably backed by a nation-state.”
According to a timeline put together by Dragos, the attack began when hackers compromised the personal email address of a recent hire in the company’s sales team. The employee had not started work yet and had not finished the onboarding process or set up two-factor authentication for their employee account.
Once the attackers had access to the employee’s email, they accomplished the initial steps in the onboarding. This gave the group access to sales department resources and the Dragos contract management system. One of the documents the attackers accessed was a report including IP addresses associated with a customer. Dragos did not identify this client but said it had reached out to notify them.
Attempts to access other Dragos systems, including messaging, finance, employee recognition and marketing, were blocked by the firm’s automated internal security processes over the initial eight hours after the intrusion. The group was also unsuccessful in escalating their user privileges, accomplishing lateral movement into other systems, and in making changes to the company’s infrastructure.
Dragos remained unaware of the attackers’ presence until the following morning, about 16 hours after the intruders logged in to the employee’s account. At that point a member of the executive team read an email that the attackers had sent five hours earlier, attempting to extort the company to avoid public disclosure of the incident.
The attackers also sent text messages to members of the company’s leadership; some of these messages contained references to family members and contacts, demonstrating that the hackers had researched their targets thoroughly. Executives also received messages at their personal accounts, though Dragos decided “that the best response was to not engage with the criminals.”
Intruders Likely Intended Ransomware Attack
In its analysis, Dragos theorized that the attackers had planned to install ransomware on the company’s system, but switched their goal to extortion after they were unable to access a valuable target. After receiving the threatening emails, the company’s security staff identified the compromised account, revoked all of its sessions, and cut off its access to company resources.
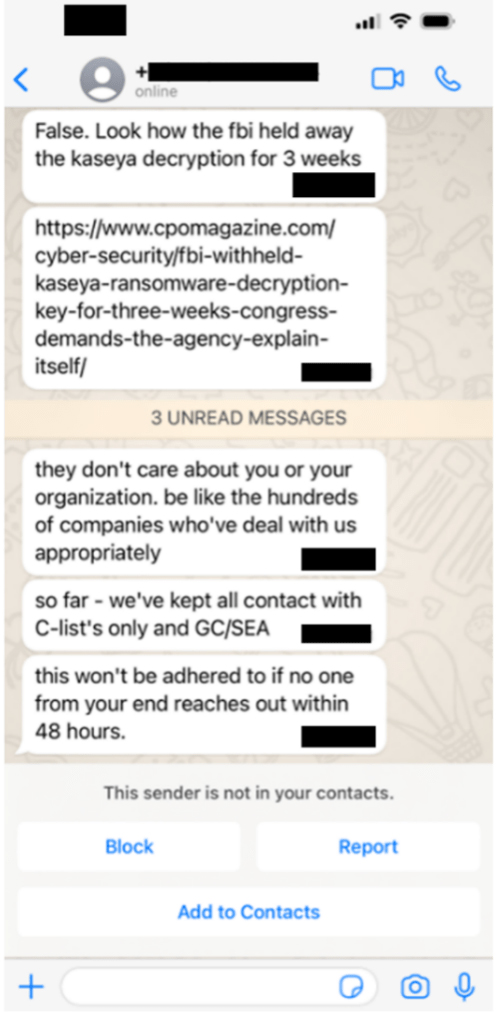 Dragos said the attackers sent this message, and others like it, to the company’s executives, trying to extort money in exchange for their silence about the security breach. | Dragos
Dragos said the attackers sent this message, and others like it, to the company’s executives, trying to extort money in exchange for their silence about the security breach. | DragosDragos listed several lessons learned from the incident. First, the company added a verification step to the onboarding process to ensure the same technique could not be used again. It is also considering expanding its use of multistep access approval because of its usefulness in blocking the intruders’ access attempts.
“The data that was lost and likely to be made public because we chose not to pay the extortion is regrettable,” Dragos said in the statement. “However, it is our hope that highlighting the methods of the adversary will help others consider additional defenses against these approaches so that they do not become a victim to similar efforts.”
Dragos CEO Robert Lee tweeted Wednesday afternoon that he was “proud of [Dragos’] security team” and that the company hoped sharing the story would “help other organizations prepare.” Dragos tweeted the knowledge that security companies can suffer breaches would help to “destigmatize security events” while making other organizations take the threat seriously.
As for the initial phishing target who served as the attackers’ entry into the company’s network, Lee tweeted that they “will absolutely be one of our valued employees (when they get their accounts back). We don’t blame victims at Dragos and no one else should either.”
Cancel praised Dragos for informing the E-ISAC of the compromise immediately and encouraged entities to read the “sobering” report. He reminded attendees that “the ERO is a target” and that they should pay attention to security alerts, even when they seem overwhelming.
“It’s easy to get desensitized to [those] alerts, but don’t let that happen,” Cancel said. “Every alert requires people looking and taking action. And that’s something that we [will] continue.”



