With threat actors becoming more aggressive and sophisticated in their tactics, companies must be prepared for hard decisions after a data breach, a cybersecurity lawyer told attendees of a webinar hosted by the Texas Reliability Entity.
Speaking at Texas RE’s regular Talk with Texas RE event Aug. 26, Rebecca Jones, a partner at cybersecurity-focused law firm Mullen Coughlin, said over the past three years, the firm has seen a steady rise in the number of data breach incidents it handles — from just under 3,000 incidents in 2022 to more than 4,200 in 2024. In the first six months of this year Mullen Coughlin dealt with more than 2,100 incidents.
The most common type of event that Jones and her colleagues have dealt with since 2022 is a business email compromise. These attacks, constituting 34 to 38% of the firm’s business each year, involve malicious actors gaining control of an official company email and using it to trick real employees into sharing sensitive information or credentials.
Ransomware is the next most common incident type, with 23 to 26% of events handled each year. Jones said this style of attack has become more elaborate recently, with a growing incidence of what the firm calls “double extortion” — cases in which the threat actor encrypts a target’s files so that they are inaccessible until a ransom is received, while also copying the data to use for their own ends.
“Threat actors [are] increasingly becoming more aggressive with their victim companies and engaging in harassment tactics to get them to pay the demand, or at least to engage in negotiations,” Jones said. “That might look like a threat actor calling employees, calling the CEO, calling board members on their cell phones, letting people know that there has been an attack and … threatening to expose data publicly, on the dark web or on the regular internet.”
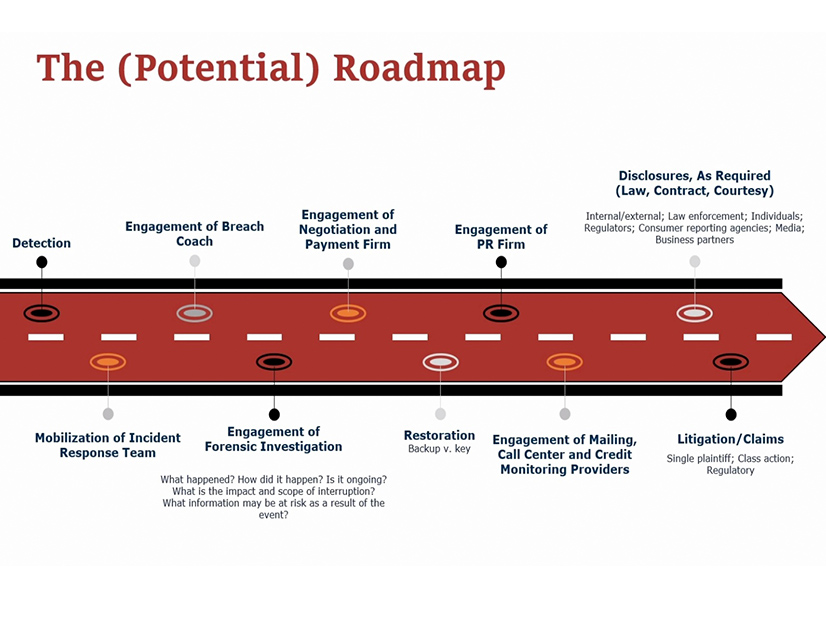
In any incident, Jones said victims need to be ready to protect their interests; the incident response team is “really the meat and potatoes of the firm,” accounting for most of the attorneys there. She presented a potential “road map” for such a scenario, outlining steps the firm’s clients have taken from the beginning to the end of the process.
The map starts with the detection of a compromise, followed by mobilizing the victim’s incident response team and following its process for restoration of data if necessary. An outside forensics team may be engaged to investigate the cause of the incident.
While the forensic investigator may also be tasked with negotiating with the attackers themselves, Jones said companies often prefer to hire a separate negotiating team with experience in such incidents. Although many companies end up paying the ransom to recover their systems, a good negotiator can usually bargain a payment down from an initial extreme figure to one that is more manageable, she explained.
The firm will usually recommend that victims hire a public relations firm as well, ensuring that their communication is accurate and does not trigger unnecessary obligations. Companies must comply with the legal disclosure requirements, Jones emphasized, but they should also be aware of the impact that their public messaging has.
“We don’t use the term ‘breach’ if we can avoid it … because it’s something that people will say without knowing what it means,” Jones said. “A breach means that there was unauthorized access or acquisition of legally protected information, and you have to notify individuals and probably regulators. Saying that you have a breach can imply that you have all of these obligations, so it’s not something that you would want to use at the outset of an incident when you may not even have a breach.”



