By Rich Heidorn Jr.
Two cybersecurity firms on Monday disclosed what may be the most dangerous cyber threat yet to U.S. power systems: malware that can take control of circuit breakers without any manual involvement.
Maryland-based Dragos and ESET, a Slovakian anti-virus software provider, said the malware — which the former is calling CrashOverride and the latter Industroyer — was likely the cause of a disruption last December that cut about one-fifth of Kiev’s power consumption for about an hour.
Unlike the December 2015 hack of the Ukraine system — caused by the BlackEnergy program that took advantage of vulnerabilities in Microsoft Office and required manual intervention to control circuit breakers — the new threat takes advantage of the simplicity of supervisory control and data acquisition (SCADA).
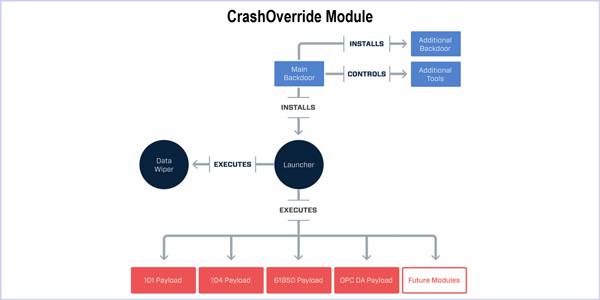
Dragos said CrashOverride is the first malware framework designed specifically to attack electric grids and the fourth ever piece of malware tailored for industrial control systems. It follows BlackEnergy 2, Havex and Stuxnet, the last of which was believed deployed by the U.S. to hack centrifuges used in Iran’s nuclear weapons program.
Dragos founder Robert M. Lee told Reuters that the malware could be used to attack power systems across Europe as is and in the U.S. “with small modifications.” It could cause outages of up to a few days in portions of a nation’s grid, he said.
The program can be detected if utilities monitor their networks for abnormal traffic, such as indications that it is searching for the location of substations or sending messages to breakers, according to Dragos.
The program’s “dangerousness lies in the fact that it uses protocols in the way they were designed to be used,” wrote Anton Cherepanov, senior malware researcher for ESET. “The problem is that these protocols were designed decades ago, and back then industrial systems were meant to be isolated from the outside world. Thus, their communication protocols were not designed with security in mind. That means that the attackers didn’t need to be looking for protocol vulnerabilities; all they needed was to teach the malware ‘to speak’ those protocols.”
Cherepanov said the program can remain undetected and eliminate traces of itself after its work is complete.
“For example, the communication with the [command and control] servers hidden in Tor can be limited to non-working hours. Also, it employs an additional backdoor — masquerading as the Notepad application — designed to regain access to the targeted network in case the main backdoor is detected and/or disabled,” Cherepanov wrote.
Part of the “dark web,” the Tor network allows users to access the Internet through “virtual tunnels” rather than making a direct connection, allowing them protect the privacy of their communications. It has been used to circumvent government censorship and by journalists to communicate with whistleblowers and dissidents. The U.S. Department of Homeland Security said TOR IP addresses were used by the Russian hackers who stole data from the Democratic National Committee before last year’s presidential election.
“What makes this thing a holy-crap moment is the understanding of grid operations encoded within it,” Lee told the Daily Beast. The program can run continuously, requiring manual overrides to interrupt it. “It’s like a popup on a website, where you close it and it just keeps opening again. That’s what they’re doing to circuit breakers.”
In a statement Monday from Marcus Sachs, chief security officer for the Electricity Information Sharing and Analysis Center (E-ISAC), NERC said it is aware of the threat but that “there are no reported instances of the malware in North America.”
NERC said it will update its Ukraine Defense Use Case report, issued in March, to reflect the new information.
“There is no question that cyber threats like the one in Ukraine are real and that constant vigilance is needed to protect the reliability of the North American grid,” Sachs said.
It is not certain who authored the malware.
Dragos tied it to a group called Electrum, the same group behind the 2015 Ukraine attack that left 225,000 customers in the dark. The group is believed to be tied to the Russian government. (See How a ‘Phantom Mouse’ and Weaponized Excel Files Brought Down Ukraine’s Grid.)
But a spokesman for Ukraine’s state cyber police told Reuters it had not been able to confirm Dragos’ claim because the security firms hadn’t provided authorities with samples of the code they analyzed.
Lee told The Washington Post the outages caused by CrashOverride would probably not last more than a few days in the U.S. because the electric industry is prepared to respond to disruptions from violent weather. “They’re used to having to restore power with manual operations,” he said. While it is “a significant leap forward in tradecraft, it’s also not a doomsday scenario.”