The barrier to entry for malicious cyber actors to target operational technology and industrial control systems (ICS) continued to drop in 2024, paving the way for new adversaries to target electric utilities and other critical infrastructure providers, cybersecurity firm Dragos claimed in its annual Year In Review report released Feb. 25.
At the same time, cyber defenders made “incremental but uneven” progress adapting to the new pressures on them, Dragos said, with electric utilities and other regulated industries demonstrating “higher maturity levels” than peers in other sectors, including water utilities and manufacturers. The firm said “visibility into OT environments lags behind adversary tactics in many cases.”
“Organizations with strong incident response capabilities, defensible architectures, secure remote access protocols and robust network monitoring are far better positioned to reduce the risk of a successful attack on the enterprise OT even in this increasingly complex environment,” Dragos said.
Dragos publishes its Year in Review to alert cybersecurity professionals to trends in cyberattacks, as well as specific threat groups that were active during the previous year. The firm said nine of the 23 threat groups that it tracks were active in 2024.
New Adversaries with Stage 2 Capabilities
Two of these groups — Graphite and Bauxite — were identified last year for the first time, although Graphite is known now to have been active since at least 2022, and Bauxite since 2023.
Graphite has conducted spear-phishing campaigns — in which an emailer attempts to gain confidential information by impersonating trusted senders — against natural gas pipeline operators and hydroelectric facilities in West Asia and Eastern Europe, along with energy and government entities in Poland, Ukraine and the Middle East.
While Dragos does not link attack groups with specific nation-states in its report, the firm did note that “Graphite focuses on organizations with relevance to the military situation in Ukraine.”
According to the report, Graphite’s activities have not yet risen past Stage 1 of the ICS kill chain, a model of ICS attacks adapted from Lockheed Martin’s cyber kill chain framework. SANS Institute defines Stage 1 as “espionage or an intelligence operation.” But the other newly identified group, Bauxite, has demonstrated the ability to reach Stage 2 of the kill chain, Dragos said, meaning “a capability that can meaningfully attack the ICS.”
Bauxite’s first campaign affected nearly 100 organizations globally and involved compromises of programmable logic controllers connected to the internet. This gave the attackers the ability to launch a denial-of-service attack against the victims’ ICS. The group went on to target devices manufactured by Sophos, leading to “enterprise impact on chemical, food and beverage, and water and wastewater industries.”
Dragos noted Sophos devices also are found in North American electric and oil and natural gas utilities, though these were not identified as having been affected by the attack. The firm said Bauxite “shares substantial technical overlaps, based on capabilities and network infrastructure, with the pro-Iranian hacktivist persona CyberAv3ngers.”
Three other active threat groups demonstrated ICS cyber kill chain Stage 2 capability: Chernovite, developers of the ICS attack framework Pipedream; Electrum, previously involved in attacks against Ukraine’s electric grid in 2016; and Voltzite, a group with “extensive technical overlaps with” the China-connected Volt Typhoon group. Volt Typhoon has been accused of embedding itself in the information technology networks of U.S. critical infrastructure organizations for at least five years. (See CISA Leader Reiterates China Cyber Warnings.)
Dragos called Voltzite “arguably the most crucial threat group to track in critical infrastructure, [with a] dedicated focus on OT data.” The firm said it has observed Voltzite stealing “data that contains critical information about the spatial layout of energy systems” and expects the group to continue operating against critical infrastructure both in the U.S. and “Western-aligned nations” in 2025.
Dragos Urges Ransomware Preparedness
Ransomware remained a serious threat across industries in 2024, with Dragos saying the number of ransomware attacks against industrial organizations has doubled year over year since 2022.
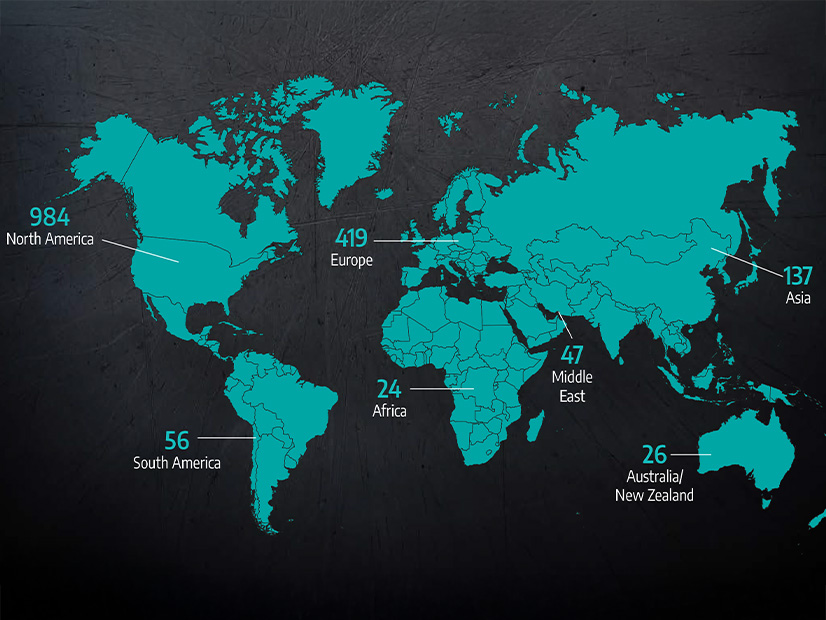
Last year, the firm observed ransomware groups posting sensitive data of 1,693 industrial organizations on their dedicated leak sites; 984 incidents, more than half the total, were observed in North America, with 419 in Europe and 137 in Asia. Fewer than 100 incidents each were observed in South America, Africa, the Middle East, and Australia and New Zealand.
Companies in the electricity industry constituted a relatively small portion of the ransomware attacks, with only 30 incidents in 2024. The vast majority of incidents affected the manufacturing sector, which Dragos attributed to the knowledge that “even brief disruptions can cause significant financial and logistical fallout” for manufacturers. However, the firm warned that other sectors, including energy, transportation and ICS vendors, “remain high on the list as ransomware groups refine their tactics to maximize pressure and impact.”
“With these threats showing no sign of slowing, organizations must prioritize resilience, proactive defenses and incident response readiness,” Dragos said.