
The cybersecurity landscape in 2021 was marked by an escalation of both known cyber vulnerabilities in U.S. industrial organizations and activity groups seeking to take advantage of those weaknesses, according to an analysis released by cybersecurity firm Dragos on Wednesday.
At the same time, the company said North American electric utilities were “very successful” over the year at taking action to safeguard their industrial control systems (ICS) and operational technology (OT) computer networks from the emerging global threats.
 Dragos CEO Robert Lee | Dragos
Dragos CEO Robert Lee | Dragos
Dragos CEO Robert Lee attributed the sector’s success partially to a history of taking the danger of cyberattacks seriously, but said a more direct cause of its resilience in 2021 was utilities’ positive response to the Biden administration’s “100-day sprints” for a range of critical infrastructure systems.
Biden’s initiative was launched in July for most sectors, but it started in April for the electric industry. (See Biden Reinstates Trump Supply Chain Order.) That effort, led by the Department of Energy’s Office of Cybersecurity, Energy Security and Emergency Response, encouraged utilities to invest in technologies to allow near-real-time situational awareness and response capabilities in ICS and OT networks, deploy procedures and equipment to enhance detection capabilities, and improve the cybersecurity posture of critical infrastructure information technology networks.
“What was very beneficial with the presidential 100-day sprints is they said … ‘We’ve heavily invested in preventative measures, firewalls, segmentation, antivirus passwords, all that kind of stuff, [but] we don’t have a lot of ability to detect and respond to threats,” Lee said in a media call introducing the firm’s 2021 Year in Review. “So we don’t care how you get it done; we just care that you get something in place to start getting insights inside … these OT or ICS networks, to where you can start finding issues, risks, threats, and sharing those insights to the government.”
The report did not directly identify how many cyberattacks in 2021 were directed at particular industries, outside of ransomware. In this area, the firm registered 13 incidents involving the energy sector. By comparison, twice as many incidents affected the transportation sector and nearly three times as many impacted food and beverage companies. Manufacturing was hit hardest, with 211 incidents in 2021; of those, less than three involved goods manufactured for the energy sector.
Threat Landscape Remains Active
This is not to say that electric utilities can rest easy. Two of the three new activity groups Dragos identified last year directly target the energy sector. One, which the firm has dubbed Kostovite — in keeping with its practice of not associating threat actors with nation-states — focuses on North America and Australia, while another, Petrovite, focuses on Central Asia.
Kostovite is seen as the more mature of the two, having reached stage 2 of the ICS kill chain, a model of ICS attacks adapted from Lockheed Martin’s cyber kill chain framework. A 2015 white paper from SANS Institute describes stage 1 of such an attack as “espionage or an intelligence operation.” In stage 2, an attacker must “specifically develop and test a capability that can meaningfully attack the ICS.”
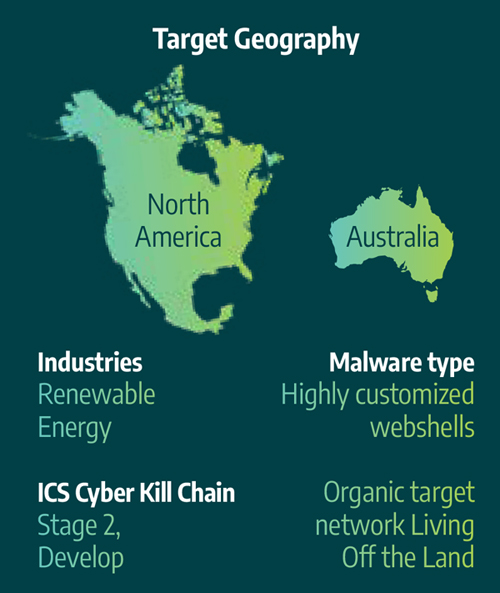 Characteristics of the Kostovite group, identified by Dragos last year, which focuses on the renewable energy industry in North America and Australia | Dragos
Characteristics of the Kostovite group, identified by Dragos last year, which focuses on the renewable energy industry in North America and Australia | Dragos
Dragos first identified Kostovite when responding to an attack on “a major renewable energy operation and maintenance firm” with facilities in North America and Australia. The attackers first gained access to legitimate account credentials, which they then used to gain access to multiple generation facilities. Once inside, Kostovite made its way around the network without using any outside tools or code, which Lee observed denotes a high level of skill. The group was able to hide inside the network undetected “for at least a month.”
The firm also pointed out that some concerning security practices are still often found among electric utilities, with limited visibility into OT and ICS networks rated as “frequent” occurrences; poor maintenance of security perimeters and allowance of external connectivity to secure systems were both considered “common,” and only shared credentials among staff ranked as “uncommon.”
By contrast, in the nuclear industry only limited visibility was rated as “frequent,” while the other three categories were considered “rare,” the lowest rating. On the other hand, the rail and food and beverage industries both saw all four categories listed under “frequent.”

