The cyber threat landscape in 2022 included new malware targeting the electric industry with “breakthrough escalation in capabilities,” in addition to an increase in energy sector-targeting threat activity in general, possibly linked to tensions between Russia and the EU, cybersecurity firm Dragos said in its annual Year in Review report released last week.
However, while attacks against targets in Europe — particularly Ukraine — escalated following Russia’s invasion of that country in February, cyber incidents involving U.S. energy utilities were “primarily focused on reconnaissance,” Dragos said. This ran counter to fears that the Russo-Ukrainian War could become the prelude to a broader cyber offensive against Western countries that support Ukraine. (See Experts Warn Cyberwar Still Possible.)
The biggest news for Dragos on the malware front last year was the introduction of Pipedream, a framework for attacks on industrial control systems (ICS) disclosed by Dragos in April. (See Dragos Warns Malware Developers Building Skills Fast.) Pipedream’s developers, a newly identified threat group dubbed “Chernovite” by Dragos, intended the tool to “attack industrial infrastructure,” the firm said.
Dragos added that it has “high confidence” that Chernovite represented a state-backed actor with “disruptive or destructive” goals, though in keeping with its usual practice, it has not connected the group with a specific nation.
 Ransomware incidents by sector | Dragos
Ransomware incidents by sector | Dragos
Although it was discovered before being deployed in the wild, Pipedream sparked concern across the cybersecurity community because of the unprecedented level of sophistication it displayed. Pipedream’s modular nature meant it could be easily modified to attack many manufacturers and equipment types and could impact companies in a wide range of industrial sectors.
Dragos’ report compared the new tool to Havex, a malware variant discovered in 2013 that targeted victims in the U.S. and Europe. Like Pipedream, Havex could be used across multiple industries; Dragos called it “the [cybersecurity] industry’s first glimpse into the potential cross-industry impact an adversary could have by taking advantage of a standard protocol.”
“Havex’s campaign goal was espionage, and … the adversary gathered data on networks from companies in the energy, aviation and pharmaceutical sectors, to name a few,” Dragos said. “While we can never know whether Chernovite looked at Havex when designing Pipedream, we do know that Pipedream takes that cross-industry ability to the next level [with] the ability to target thousands of devices across critical industries.”
Aside from Chernovite, and another newly identified threat actor dubbed “Bentonite” that targets governments and the manufacturing and maritime oil and gas networks, Dragos identified a number of other known threat groups as still active last year. These include Kostovite, which has demonstrated “skilled lateral movement and initial access operations into ICS/OT [operational technology] environments” in U.S. energy companies, and Kamacite, which has been linked to the 2015 and 2016 attacks on Ukraine’s power grid.
Electrum, another group involved in the 2016 Ukraine attacks, was back last year as well. In a fresh attack on Ukraine, the group deployed a malware that Dragos has labeled Industroyer2, a variant of the tool used in 2016. However, unlike the earlier attack, last year’s hack was apparently foiled before any outages were caused. (See E-ISAC Warns of Escalating Russian Cyber Threats.)
Ransomware on the Rise
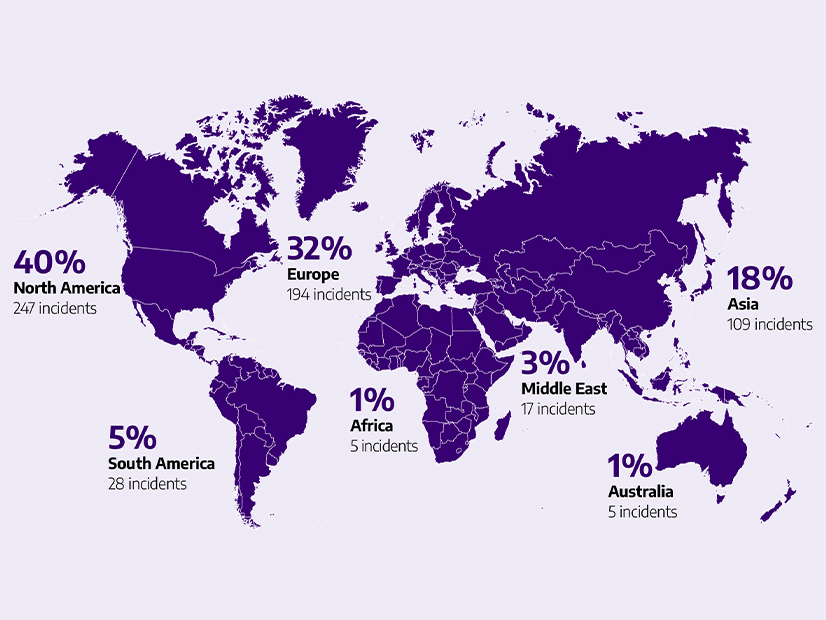
While North America was relatively free of ICS attacks during 2022, ransomware was another story. Dragos said it “tracked 605 ransomware attacks against industrial organizations [worldwide in] 2022, an increase of 87%” over the prior year. Of these, 247, or about 41%, affected organizations in North America.
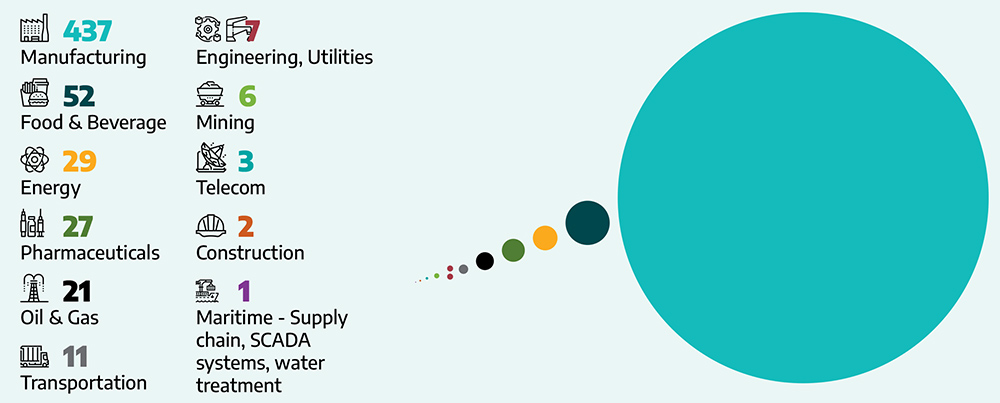
The vast majority of global ransomware incidents occurred in the manufacturing sector, with 437 attacks. Energy accounted for 29 incidents, with seven attributed to engineering and utilities.
Attacks in the energy sector included a compromise of unspecified companies reported in October by the Electricity Information Sharing and Analysis Center, resulting in the exfiltration of data that could “allow a capable adversary to dynamically model electricity systems.” According to Dragos, however, no outages are known to have occurred because of this data extraction.
The ransomware sector was marked last year by the apparent collapse of the Conti cybercrime gang in May, after its attack on the government of Costa Rica led the U.S. State Department to announce a reward for any information about the group’s leadership and affiliates. (See Dragos: Ransomware ‘More Impactful’ in Q2.)
However, the disappearance of Conti was accompanied by the rise of other groups such as Black Batista, which attacked U.S. agricultural equipment manufacturer AGCO in May; Dragos said it is possible that personnel from Conti may have joined Black Batista or other groups.
Dragos attributed about 28% of ransomware incidents last year to the Lockbit group, which released an updated version of its eponymous ransomware-as-a-service software that included features such as anti-detection mechanisms and the ability to disable Microsoft Defender Antivirus. The firm said it had “moderate confidence” that Lockbit “will pose a threat to industrial operations into 2023.”