SolarWinds
A major supplier of enterprise software has disclosed a long-term security breach, leaving the public and private sectors scrambling to respond.
In two Notices of Proposed Rulemaking issued at its open meeting, FERC proposed to approve 11 new Critical Infrastructure Protection standards intended to allow utilities to use virtualization technology.
NERC and the regional entities expressed support for FERC's cybersecurity proposals but reminded the commission of their already busy development cycle.
FERC issued two NOPRs indicating it will direct NERC to develop new cybersecurity standards.
NERC submitted to FERC its proposed cybersecurity reliability standard requiring utilities to implement internal network security monitoring software on select grid cyber systems.
Registered entities must report to NERC on the cyber assets present on their systems and the potential impact of adding security monitoring software.
FERC ordered NERC to require utilities to implement internal network security monitoring on certain cyber systems at bulk power system facilities.
NERC's 2021 Annual Report identified climate change and cybersecurity as major risks to grid reliability, while highlighting efforts to combat them.
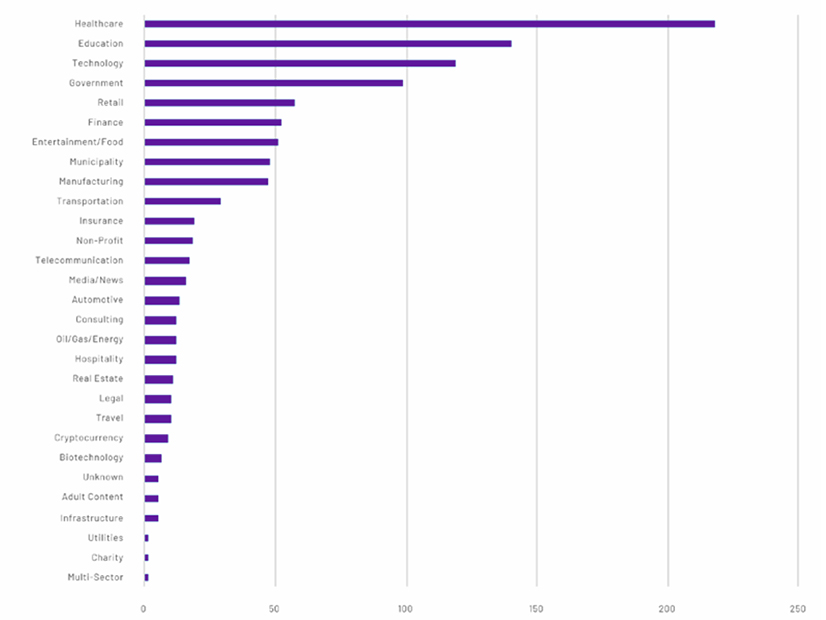
A new report from cybersecurity firm Tenable warns that critical infrastructure and other sectors must tackle the vulnerabilities found in common platforms.
As fears of Russian military action against Ukraine rise, the U.S. government is urging cyber readiness at the nation's critical infrastructure operators.
Want more? Advanced Search