A handful of high-profile cyberattacks grabbed headlines last year, but cybersecurity advisory firm Tenable said in a report this week that the biggest challenge for the security community continues to be “age-old security challenges in new infrastructure.”
“Organizations continue to struggle with protecting, or even defining, the perimeter. Migration to cloud platforms, reliance on managed service providers, software and infrastructure as a service have all changed how organizations must think about and secure the perimeter,” the 2021 Threat Landscape Retrospective said. “Fragmented security solutions and poorly defined security outcomes must be left behind to match the complexity of the modern attack surface.”
Tenable’s goal was to highlight the security issues that plagued the public and private sector last year. While big events drew most of the public’s attention last year — for example, the compromise of the SolarWinds Orion network management software that began in December 2020, and the ransomware attack against Colonial Pipeline in May — the firm said these hacks were the tip of the iceberg, with 1,825 total breach events detected from Nov. 1, 2020 to Oct. 31, 2021.
OT, IT in ‘Attackers’ Crosshairs’
While details on many of last year’s cyber incidents have not been disclosed due to security and privacy concerns, or the desire of companies involved to avoid embarrassment, Tenable’s analysis shows more than 260 terabytes of data was stolen comprising 1.8 billion files, documents or emails.
About 38% of all breaches that Tenable analyzed were the result of ransomware attacks, such as the one against Colonial that led to the shutdown of the company’s entire pipeline network and stifled the flow of petroleum products to the U.S. East Coast. (See Colonial CEO Welcomes Federal Cyber Assistance.) Meat supplier JBS suffered a similar ransomware attack; like Colonial, its leadership decided to pay the attackers to unlock their computer systems and prevent the release of sensitive data. The two companies’ ransoms amounted to the equivalent of around $16 million.
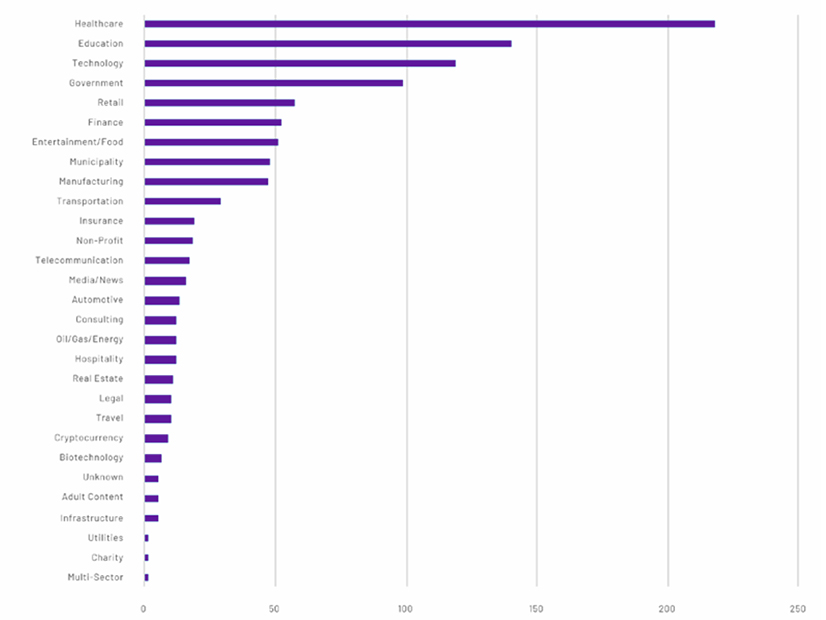
While the Colonial and JBS breaches garnered national attention and concern at the highest levels of government, the energy, infrastructure and utilities sectors accounted for only a small fraction of ransomware attacks and total breaches. As in 2020, Tenable found that attacks fell most heavily on the healthcare sector, which accounted for nearly a quarter of the year’s total events, followed by education, with 13%.
However, the firm warned that utilities and other critical infrastructure operators should not rest easy, since last year’s incidents “proved that information technology (IT) and OT [operational technology] environments are in attackers’ crosshairs,” along with critical infrastructure. And since many of the same software tools are used across multiple industries, successfully breaking into one common platform can render all its users vulnerable.
This is what happened with the SolarWinds hack, in which the breach of the Orion software — now attributed to Russia’s Foreign Intelligence Service — may have exposed the information of thousands of customers, including the Department of Energy and FERC. (See FERC, E-ISAC Report Details Reach of SolarWinds Compromise.) The same hackers have since been blamed for additional attacks, including breaches of Microsoft and computer services provider Pulse Connect Secure.
Zero-days Across Common Software
A common point of entry for hackers are zero-day vulnerabilities, defined by Tenable as software or hardware flaws that are “unknown to a vendor prior to [their] public disclosure, or [have] been publicly disclosed prior to a patch being made available.” The firm identified 105 zero-day vulnerabilities in 2021, of which 83% are known to have been exploited in the wild. The report said that details of these weaknesses “are often kept under wraps” to prevent them from being exploited.
Two-thirds of the discovered vulnerabilities originated with just three companies: 28% in Microsoft products, 21% from Apple, and 18% from Google. Thirty percent of the vulnerabilities were detected in web browsers and 26% were in operating system software, with the rest found in web apps, email clients, office suites and other software products.
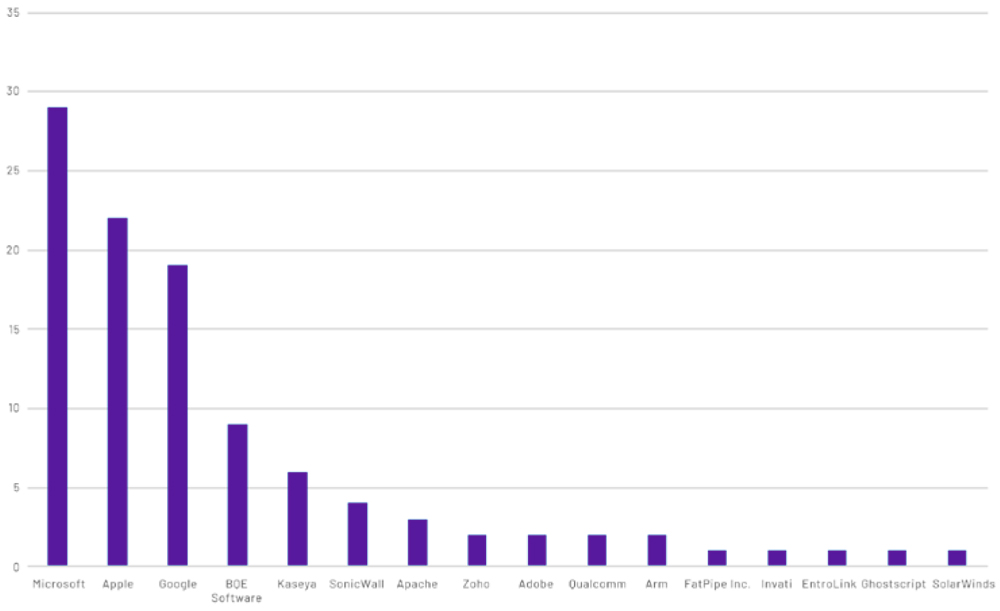 2021 zero-day vulnerabilities by vendor | Tenable
2021 zero-day vulnerabilities by vendor | Tenable
Tenable warned that while these vulnerabilities are “primarily leveraged in limited, targeted attacks” and therefore usually have limited impact at first, cybersecurity professionals cannot afford to disregard their dangers.
“The true value of a zero-day vulnerability is often not defined by its exploitation prior to discovery, but by the blog posts and proof-of-concept code published in the weeks and months after disclosure,” Tenable said. “Zero-day vulnerabilities typically become more problematic for most organizations after they’ve made the transition to legacy status, particularly if an organization has not yet applied available patches before widespread exploitation begins.”