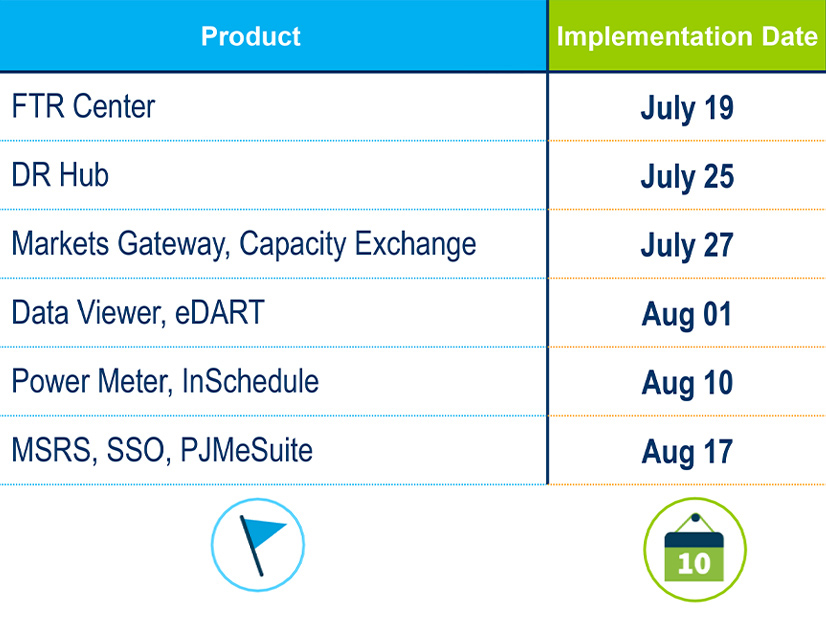
VALLEY FORGE, Pa. — PJM will stop supporting older, less secure versions of transport layer security (TLS) encryption in its remaining applications between now and Aug. 17 because of cybersecurity concerns.
TLS protects data on websites and securely transfers data between clients and servers.
PJM Chief Information Security Officer Steve McElwee told the Market Implementation Committee on Wednesday that passwords and market data can be intercepted and decrypted in TLS 1.0 and 1.1.
The RTO disabled 1.0 and 1.1 in its training environment last year and has replaced them on several production PJM Tools applications and on PJM.com. It is expediting the transition for the remaining applications in response to a recommendation from the U.S. Department of Homeland Security. Users will not be able to access the applications unless browser and browser-less API interactions use TLS 1.2.
“We’re really working aggressively to reduce the attack surface for adversaries,” McElwee said. “We had longer-term plans to let you adapt, but we had to accelerate that. We recognize that could cause some impact for you.”
McElwee said about 98% of PJM stakeholders have already adopted the new TLS. “It’s that 2% that we really want to track down,” he said.
Russian Threats
McElwee repeated his briefing about the changes before the Operating Committee on Thursday, saying that “if you get a communication from us, it’s not a phishing attempt. It is legitimate.”
He also told the OC of other cybersecurity issues, including a June 22 Microsoft intelligence report that said the software maker had detected Russian network intrusion efforts on 128 organizations in 42 countries outside of Ukraine.
Pro-Russia groups have been linked to many distributed denial of service (DDoS) attacks, he said, including a cyber collective called Killnet that claimed responsibility last month for DDoS attacks in Lithuania in response to the closure of transit routes within the Russian exclave of Kaliningrad.
PJM is following DHS’ “shields up” recommendations, including blocking international and anonymized network traffic and exercising incident-response plans.
“We recognize the threat of retaliation against the U.S. is very real, so we’re [doing what we can] to stay on guard against that threat,” McElwee said.
He recommended reading the Cybersecurity and Infrastructure Security Agency’s May alert on threats to managed service providers and their customers, and its June warning on exploits targeting VMware Horizon and Unified Access Gateway servers.
He also urged PJM member companies to use measures such as multifactor authentication to protect their email systems. “Business email compromise can have a lot of impact on your organization,” he said. “A cyberattack against one of us could affect all of us.”
GMD Vulnerability Analysis Update
PJM’s Stanley Sliwa told the Planning Committee on July 12 that the RTO hopes to complete its assessment of its vulnerability to geomagnetic disturbances (GMDs) by the end of the year.
NERC reliability standard TPL-007-4 requirement R3 requires the RTO to establish acceptable steady-state voltage performance for its system during a GMD event, and prevent a voltage collapse and cascading and uncontrolled islanding.
But it allows loss of generation, transmission configuration changes and re-dispatch of generation if time permits. Also permitted are interruptions of firm transmission and manual or automatic load shedding.
Voltage performance is examined in three stages, beginning with the posturing of the system in response to space weather information warning of a potential GMD. “If we know PJM is expecting a GMD, certain actions can be taken to prepare the system,” Sliwa explained.
Performance also is measured after the onset of the event, but prior to loss of elements. The final measurement is made after the potential loss of reactive power compensation devices and other transmission facilities as a result of protection system operations or misoperations during an event.

