FERC’s June order approving NERC’s internal network security monitoring reliability standards has prompted another request for clarification from the ERO, which seeks to “eliminate ambiguity regarding the intended scope of the commission’s directive” (RM24-7).
NERC’s July 25 filing was a response to the commission’s Order 907 issued June 26, which approved CIP-015-1 (Cybersecurity-INSM). The standard requires utilities to implement INSM for all high-impact grid-connected cyber systems with or without external routable connectivity (ERC), as well as medium-impact systems with ERC. It was meant as a precaution against events like the SolarWinds hack of 2020, in which hackers used a common network management tool to push malicious code to customers worldwide. (See FERC Approves NERC’s Proposed INSM Standard.)
In a response to a Notice of Proposed Rulemaking in November 2024, NERC had requested clarification on the term “CIP [critical infrastructure protection]-networked environment,” a term FERC used in the NOPR, calling on the ERO to protect “all trust zones of the CIP-networked environment,” but did not define.
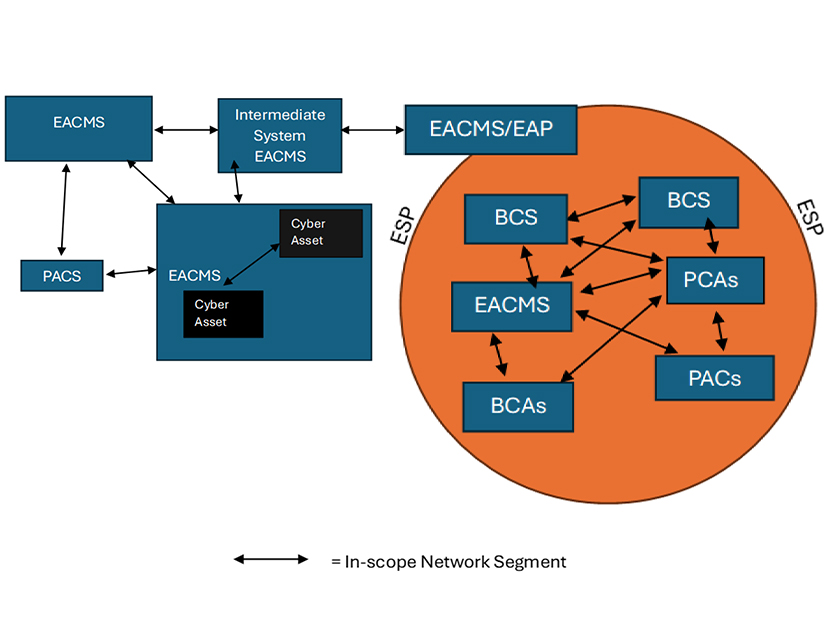
FERC said in Order 907 that the term “does not cover all of a responsible entity’s network.” But it does include “the systems within the electronic security perimeter [the electronic border around an internal network] and network connections among and between electronic access control or monitoring systems (EACMS) and physical access control systems (PACS) external to the [ESP].”
Having established this definition, FERC directed NERC to update the standard to “extend INSM implementation to EACMS and PACS” outside of the ESP, giving the ERO 12 months from the effective date of the order (meaning Sept. 1, 2026) to file the modified standard. However, NERC claimed in its most recent filing that it still needed clarification to understand the scope of the order “and facilitate a timely development process.”
First, the ERO asked FERC to explain whether “only the communication paths between the CIP devices” are included in the term, or whether it applies to “all communications on the network segment.” Referring to a graphic the commission included in its order, NERC noted that “non-CIP cyber assets outside” of the ESP are not included, contrary to the text of the order, which includes “network segments that are connected to EACMS and PACS outside” of the ESP. NERC said clarification on this point is needed in order to address the commission’s directive.
Second, the ERO requested that FERC specify whether communication between PACS and non-PACS controllers are part of the CIP-networked environment. NERC observed that Order 907 refers to “communication between PACS and controllers and communications to and from EACMS used solely for electronic access monitoring,” without providing clarity on whether non-PACS controllers are included.
“Addressing these questions about the [order’s] intended scope … will provide the [standard] drafting team a clear direction, thus promoting a timely development process that develops revisions that are responsive to the commission’s intent,” NERC said.
CIP-015-1 is set to take effect 60 days from the publication of Order 907 in the Federal Register, or Sept. 2.



