FERC has replied to a request for clarification from NERC on its directive that the ERO revise the recently approved reliability standard requiring utilities to implement internal network security monitoring (INSM) at some grid-connected cyber systems.
FERC provided NERC the information it requested while denying a request from several trade organizations for a technical conference to provide further clarity (RM24-7).
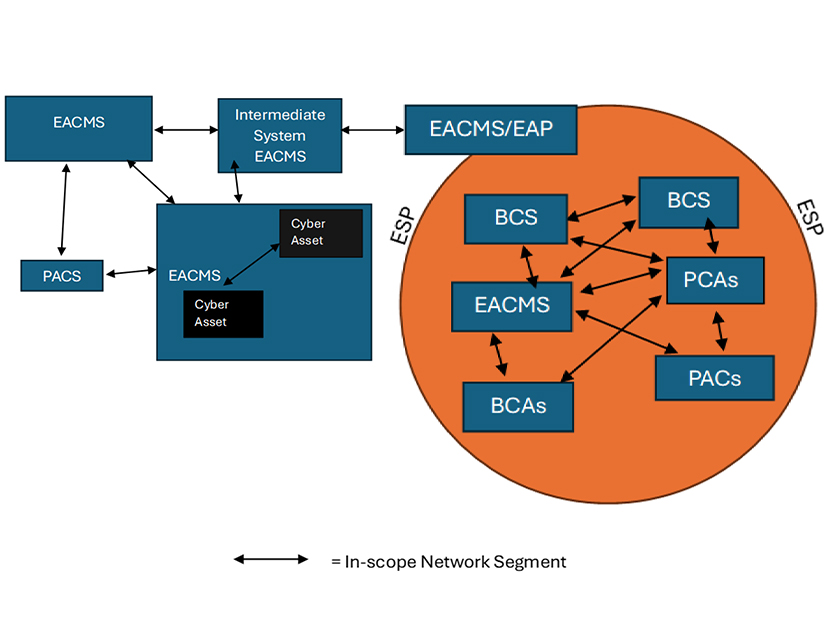
The commission approved CIP-015-1 (Cybersecurity — INSM) on June 26, 2025; the standard requires utilities to implement INSM for all high-impact grid-connected cyber systems with or without external routable connectivity (ERC), as well as medium-impact systems with ERC. (See FERC Approves NERC’s Proposed INSM Standard.) FERC directed the standard’s development in response to the SolarWinds hack of 2020, in which malicious actors infiltrated the update channel of a common network management tool to push malicious code to customers worldwide.
Along with its approval of the new standard, FERC directed NERC to make further changes, due 12 months after the effective date of the final rule, requiring that utilities extend the implementation of INSM to electronic access control or monitoring systems (EACMS) and physical access control systems (PACS) outside their electronic security perimeter, the electronic border around their internal networks.
However, NERC later filed a request for clarification seeking to “eliminate ambiguity regarding the intended scope of the commission’s directive.” (See NERC Requests Clarity on FERC’s INSM Order.) At issue was the term “CIP-networked environment,” which FERC had used in an earlier notice of proposed rule-making (calling on the ERO to protect “all trust zones of the CIP-networked environment”) without defining it.
FERC said in its order approving CIP-015-1 that the CIP-networked environment “does not cover all of a responsible entity’s network” but does include “the systems within the [ESP] and network connections among and between [EACMS] and [PACS] external to the [ESP].”
NERC asked the commission to explain whether the term refers only to communication paths between CIP devices, or if it means “all communications on the network segment.” It also requested that FERC specify whether communication between PACS and non-PACS controllers are part of the CIP-networked environment.
The request for a technical conference came from the American Public Power Association, Edison Electric Institute, and the National Rural Electric Cooperative Association, which sought to confirm that FERC’s order “does not require monitoring of network traffic between non-CIP assets and intermediate systems that are classified as EACMS.”
In its Aug. 21 filing, FERC explained that the term “is not intended to capture non-CIP assets” and that the assets specified by NERC — non-CIP cyber assets, non-PACS controllers and non-EACMS firewalls — are all out of scope. This means that “for shared network segments located outside the electronic security perimeter containing both CIP (i.e., EACMS or PACS) and non-CIP assets (e.g., corporate devices), only the east-west traffic for access monitoring of EACMS and PACS is within the scope of the term CIP-networked environment.”
Regarding NERC’s second question, FERC confirmed that because non-PACS controllers are not CIP assets, “CIP-networked environment” therefore does not include “communication between PACS and non-PACS controllers.” On the other hand, communication between PACS and PACS controllers is in scope because such communication “is considered internal traffic of the PACS.”
In light of its clarification, FERC determined that its order “is sufficiently clear on how NERC should implement [FERC’s] directives” and that a technical conference is not required. However, the commission said NERC could hold its own conference if the ERO and industry stakeholders consider it appropriate.



