By Rich Heidorn Jr.
The Transportation Security Administration’s oversight of natural gas pipeline security is hampered by staffing constraints and vague criteria for identifying critical facilities, the Government Accountability Office reported last week.
TSA’s Pipeline Security Branch, which is responsible for more than 2.7 million miles of natural gas, oil and hazardous liquid pipelines, currently has only six full-time equivalent employees. Staffing has fluctuated from a high of 14 in fiscal year 2013 to only one in 2014. The agency, part of the Department of Homeland Security, also lacks a “strategic workforce plan” to identify the skills required of its employees, such as cybersecurity expertise.
GAO also found TSA has not updated its risk assessment methodology since 2014 to reflect current threats to pipelines and that its data sources and underlying assumptions on threats and vulnerabilities are not fully documented. Its risk assessment has not been peer reviewed since it was initiated in 2007, the report said.
Although TSA issued revised guidelines in March 2018 incorporating most of the National Institute of Standards and Technology’s “Framework for Improving Critical Infrastructure Cybersecurity,” it did not include all of the framework and lacks a formal process for revising the guidelines on a regular basis. “Without such a documented process, TSA cannot ensure that its guidelines reflect the latest known standards and best practices for physical security and cybersecurity, or address the dynamic security threat environment that pipelines face,” GAO said.
Critical Facilities
The guidelines also lack clear definitions to ensure that pipeline operators identify their critical facilities — one reason, auditors speculated, that one-third of the 100 largest pipeline systems have not identified any critical facilities.
TSA’s eight criteria lack “additional examples or clarification … to help operators determine criticality,” the report said.
GAO said pipeline operators told it that pipelines may interpret one TSA criterion, “cause mass casualties or significant health effect,” differently. “One of these operators that we interviewed stated that this criterion could be interpreted either as a specific number of people affected or a sufficient volume to overwhelm a local health department, which could vary depending on the locality. Another operator reported that because TSA’s criteria were not clear, they created their own criteria which helped the operator identify two additional critical facilities.”
GAO said one unnamed industry association it met with is working with TSA to develop supplementary guidance for its members to clarify the agency’s critical facility criteria. The American Gas Association (AGA), which represents more than 200 local distribution companies, confirmed it is the group mentioned.
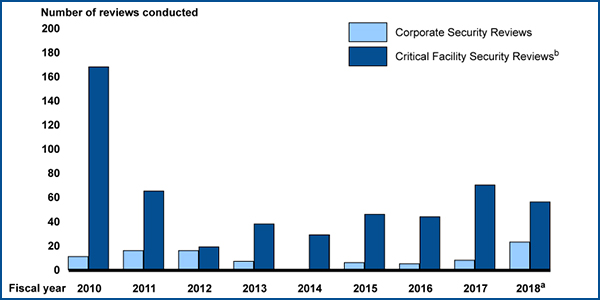
TSA conducts security reviews of the largest 100 companies, but it hasn’t checked in the last five years whether its recommended improvements are being followed, leaving it unable to know whether its efforts are reducing risks, the report said.
Based on the company reviews, TSA may also review the security on a company’s critical facilities. Although the reviews are voluntary, TSA told auditors no company has ever rejected an inspection request.
The agency conducted 23 corporate reviews and about 60 facility reviews in fiscal year 2018 (through July 31). In 2014, when the safety unit had only one FTE, it conducted no corporate reviews and about 30 facility reviews.
Dispute on Mandatory Rules
At FERC’s open meeting Thursday, Chairman Neil Chatterjee said the GAO report “reiterated” concerns he and Commissioner Richard Glick expressed in a June op-ed calling for mandatory reliability standards for natural gas pipelines like those the commission and NERC enforce on the grid. “Despite having the authority to enforce mandatory cybersecurity standards, the TSA relies on voluntary ones,” they wrote.
Glick said TSA performs a valuable role in airport security but is ill-suited for overseeing pipeline security. “I continue to believe that Congress should … consider moving authority over gas pipeline cybersecurity to another agency such as the Department of Energy.”
Chatterjee said that although the GAO report identified gaps, he has been pleased by recent efforts by industry and DHS to improve pipeline security, including the creation of a risk assessment program that includes DHS, TSA, DOE and FERC.
In a press release, Don Santa, CEO of the Interstate Natural Gas Association of America (INGAA), also cited what he called his group’s “partnership” with TSA, DHS and DOE to conduct cybersecurity assessments of pipelines, saying, “This interagency approach will bring to bear the particular expertise of each agency, along with those of the industry itself.” INGAA says its 26 members represent most of the interstate natural gas transmission pipeline companies in the U.S. and Canada.
But he rejected the idea of mandatory standards. “In this environment of rapidly evolving cyber threats, it is important that we take an approach that enables flexibility and allows us to quickly adapt and update protocols,” he said. “Experience shows that mandatory standards are all too often outdated almost as soon as they are introduced. We need the flexibility and ability to build on our baseline practices to look forward towards addressing the threats of the future.”
AGA said in a statement that GAO’s criticism “is missing the mark.”
TSA officials “understand the industry and have a strong working relationship with natural gas utilities,” said AGA CEO Dave McCurdy, who called for expanding the agency’s budget and staff “so that they can come into our member companies and make the assessments themselves. In addition to our numerous voluntary programs in the cybersecurity arena, we believe that this is the best way to build upon the success of this public-private partnership.”