By Rich Heidorn Jr.
Russian hackers gained the ability to manipulate U.S. utilities’ industrial control systems (ICS), federal officials said in a briefing Wednesday that offered the most detailed account yet of a campaign that compromised hundreds of energy companies last summer.
The campaign, which began with phishing attacks and watering hole exploits to capture the credentials of vendors trusted by the utilities, did not result in any physical impact. But it was nonetheless troubling because of the length of time the hackers lingered in the utilities’ systems and the access they gained, officials said.
The Department of Homeland Security’s “Awareness Briefing” indicated the hackers had access to the same type of human-machine interfaces that suspected Russian agents used to cause blackouts in Ukraine in 2015. (See How a ‘Phantom Mouse’ and Weaponized Excel Files Brought Down Ukraine’s Grid.)
Access but no Damage
“The punch line is this: In this campaign so far, the effect has been limited to being able to access the systems — to gain fairly sophisticated level access into the systems,” said Jon Homer, chief of the industrial systems control group for the Hunt & Incident Response Team at DHS’s National Cybersecurity & Communications Integration Center. “But … they have not caused physical impact as a result of that access. So, they had access to be able to do it, but they haven’t actually caused any physical [damage].”
Jeannette Manfra, assistant secretary for DHS’s Office of Cybersecurity and Communications, said the detection of the infiltrations — the subject of a March 15 DHS alert — was the result of the “partnership” among DHS, the power industry, the Department of Energy, the intelligence community and the FBI.
“We were able to work very closely as soon as we identified a threat and respond to that and ensure that in this case the Russians were not able to achieve any significant goal in terms of actually disrupting infrastructure,” she continued. “To be clear, there was no threat for the electrical grid to go down. … While they were in a position to be able to manipulate some systems, there wasn’t a broader threat to our entire electric grid.”
DHS held Wednesday’s webinar “to raise awareness more broadly so that others could defend against this,” Manfra said. Additional briefings are scheduled for July 30 and Aug. 1.
Hackers ‘Stuck Around’
Homer said the campaign was “an advanced persistent threat in its classic definition. We’re looking at someone at an organization that got in and stuck around.”
He said the campaign targeted or affected “hundreds of victims” focused on electric generation, transmission and distribution. “But there were also victims … in the nuclear sector, in the aviation sector, critical manufacturing, government entities.”
The targets — none of which were identified — included small, medium and large organizations selected for their “strategic placement,” Homer said. DHS said the targets’ names “align with open-source lists (organized by subject-matter areas) published by third-party industry organizations.”
Homer said the power generation, transmission and distribution companies were penetrated despite having “good, sophisticated networks from a cyber defense perspective. They have the right tools. They have the budgets. They have the capabilities to defend their networks from this effort.”
Preexisting Relationships
The campaign began in early 2016 with the penetration of the first of many “staging targets,” small organizations with less sophisticated networks such as vendors, integrators and strategic R&D partners.
“They were selected because of their preexisting relationship with the intended target,” Homer said. “This is not a target of opportunity-type campaign. This is not one where the threat actor went around and said, ‘Who forgot to patch their systems last month?’”
The campaign was dormant for more than a year after the first penetration, until early 2017, when a second vendor network was compromised. That network was used to launch a phishing attack against another vendor and government entity, allowing the hackers to move to another vendor, which was used to phish operators at the utilities. Later, the first compromised vendor was used to access several utilities and IT service providers.
Homer said the hackers used the staging targets’ networks, so when the intended targets reviewed activity logs it appeared “as if the traffic or the code was originating from … one of their trusted partners.”
Because control systems are customized for their application, it takes utilities’ technicians months to learn how to operate them. “In the same regard a threat actor who wished to manipulate a control system has to understand that particular setup, architecture and design,” Homer said.
Thus, the hackers scoured file servers “for specific file names and specific keywords — things pertaining to vendor information and reference documents.”
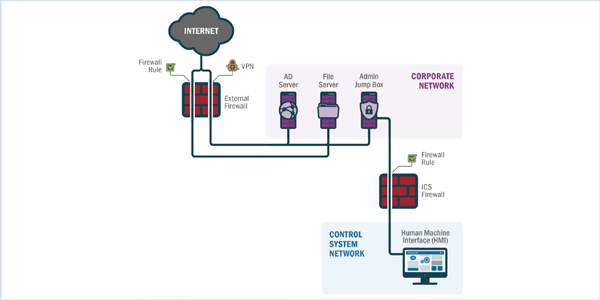
The hackers were aided because some of the companies’ “jump boxes” — computers used to authenticate access to the ICS — contained files with information such as IP addresses, ports and default user names.
The hackers also were aided by publicity photographs on some companies’ websites that inadvertently revealed security information.
“These are things like … cutting a ribbon or something like that, and there’s the CEO talking to the mayor,” Homer explained. “But in the background of the picture are control systems, and on these control systems are very important things like set points and safety guards and configurations and diagrams and all these kinds of things. All of this is very valuable information, but it’s in the background and the organization didn’t realize what they had published.”
Lessons Learned
The campaign ultimately allowed the hackers to get across the ICS firewalls and gain control of the human-machine interfaces used by the utilities’ system operators.
DHS officials concluded the initial access to corporate networks came primarily through the capture of legitimate credentials. All victims had externally-facing, single-factor authenticated systems. Intrusions came via virtual private networks, Microsoft Outlook web access and remote desktops.
Officials said the investigation illustrated the need to require multi-factor authentication for all external interfaces and to block all external server message block (SMB) network traffic. “There’s really not a good business justification for having external SMB outbound,” Homer said.